Independent Software Vendors (ISVs) and developers of payment solutions must understand the acceptable formats for truncation as required by the PCI-DSS.
The PCI-DSS (Payment Card Industry Data Security Standard) is a set of requirements designed to protect cardholder data. Merchants that store, process or transmit cardholder data are required to comply with the PCI-DSS requirements. Developers of payments solutions must develop these products for use in a manner compliant with the PCI-DSS requirements. In cases where these solutions need to store 16-digit Primary Account Numbers (PAN), solution providers need to understand the requirements of secure storage. One important thing to understand is when truncation is appropriate, and how to properly protect truncated PAN.
Are truncated Primary Account Numbers (PAN) required to be protected in accordance with PCI DSS?
Truncated PAN must be protected in accordance with the PCI-DSS requirements. The guidelines for truncation of PAN can be found in the PCI-DSS, specifically in PCI-DSS requirement 3.4.
PCI-DSS requirement 3.4 requires validating entities to render PAN unreadable anywhere it is stored. This includes electronic media, in logs, data backups and anywhere that data may be stored including wireless networks.
The PCI-DSS lays out acceptable methods that can be used to meet this requirement. They include truncation, strong one-way hash functions of the entire PAN, index tokens with securely stored pads, or strong cryptography.
PCI-DSS standards apply to merchants, service providers, and any entities involved in the storage, processing, or transmission of credit card account data. Developers of payment solutions must develop payment solutions that are designed for use in a PCI-compliant manner. Failure to appropriately protect card data can lead to large fines from Card Association members. Failure to correctly truncate PAN can lead to a security breach of cardholder account data.
If your organization deals with digital payments, stores PAN, or develops payment solutions/services that store PAN, it is important to understand the requirements around truncation of PAN data.
What is the process of truncation?
Whether you’re just getting started with PCI or you have seasoned experience with developing and vending payment software, it’s imperative to stay abreast of industry trends and regulations.
Truncation can be defined as the act of shortening something, in this case the Primary Account Number, which is the 16-digit account number traditionally embossed on the front of the payment card. It is an acceptable method of rendering cardholder data unreadable if stored, and is performed by permanently removing a portion of the data when that data is stored in files, logs, and databases.
It should be noted that truncation is a permanent process and differs from PCI-DSS requirement 3.3 (mask PAN when displayed). While truncation refers to rendering the PAN unreadable when stored, requirement 3.3 speaks specifically to temporarily masking the data when it is displayed on paper receipts or screens. There are multiple acceptable methods of truncation according to the PCI Security Standards Council, which we’ll discuss in detail below.
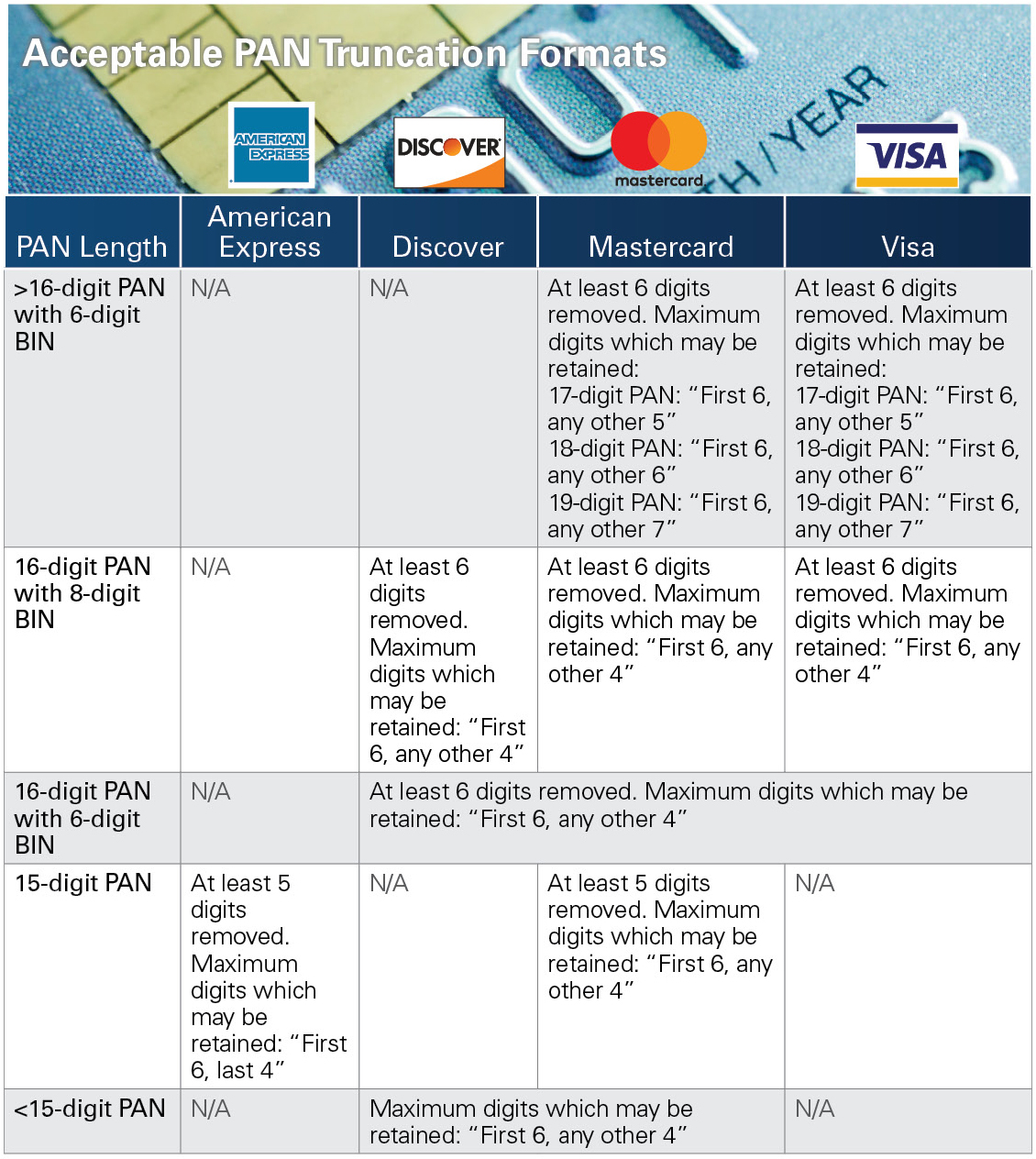
What are acceptable formats for the truncation of primary account numbers?
In order to consider PAN data truncated appropriately for storage in a PCI-DSS compliant manner, the data cannot exceed the first six last four digits of the PAN. Once the middle six digits are removed, the PAN is no longer considered cardholder data and is considered unreadable.
It should be noted that PAN and other pieces of cardholder data should only be stored if necessary for legal, business, or regulatory needs. Eliminating storage of cardholder data is an easy way to avoid having to deal with PCI-DSS requirement 3 and reduce the overall scope of a PCI-DSS validation.
The PCI-DSS specifically lays out the danger of storing truncated PAN along with a hashed version of the full PAN. It may be easy for a bad actor to reconstruct the full PAN if they have access to both the truncated and hashed version of the full PAN. In cases where PAN is present in both forms, you must introduce additional security controls to ensure the data cannot be reconstructed. This also applies if there are multiple versions of truncated PAN stored in the same environment.
PAN truncation can replace the data with an “x” or “0” in place of the truncated middle digits. Importantly, hashing cannot be used to replace the truncated segment of the PAN. The benefit is that If the transaction is intercepted, the encrypted card data is unreadable. The data means nothing to anyone other than the processor that holds the decryption key.
The industry standard is to remove the middle six digits, but there are some differences between the rules for each of the major card brands. Entities that are looking for flexibility in this area should review the individual requirements for each card brand. They must also consider the purpose for which the data will be used along with internal and external constraints.
Can hashing be used to replace the truncated segments of PAN?
Requirement 3.4 specifically details the fact that hashing cannot be used to replace the truncated data. Acceptable replacement for these digits is “x” or “0” characters. Replacing the truncated data with a hashed version makes it easy for an attacker to reconstruct the original PAN if intercepted.
What is the difference between masking and truncation?
There is often confusion between PCI requirements that prescribe truncation of data versus those that prescribe masking of data. Requirement 3.4 talks about truncation of PAN data for the purposes of storage on electronic media. Requirement 3.3 requires masking of card data wherever displayed, specifically on screens and paper receipts. Truncation of data is permanent and applies to storage of PAN; masking is temporary and applies to displays when there is no business need to see the PAN.
Conclusion
Independent Software Vendors (ISVs) and developers of payment solutions must ensure they understand the acceptable formats and requirements for truncation of PAN as required by the PCI-DSS. These requirements will help them protect their merchants from a breach of cardholder data. Contact us today to learn how we can help you with PCI compliance.

